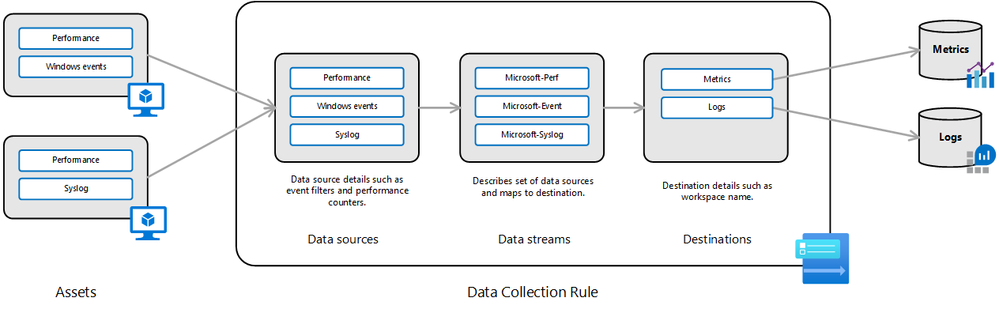
In the domain of cybersecurity, effective data collection and log management are important for detecting and responding to potential threats. This blog post delves into the utilization of AMA for data collection in Azure Sentinel, focusing on filtering custom logs using XPath queries, sending logs to destinations using Data Collection Rules (DCR), and best practices for collecting crucial event IDs. My aim is to provide actionable tips, real-life examples, and expert insights that will aid readers in optimizing their security operations while managing costs effectively.
Securiment Blogs
The approved contractor of Cyber Security Solutions, providing quality services to many organizations & private companies