Microsoft Defender for Identity
1. Introduction
Microsoft Defender for Identity (formerly Azure Advanced Threat Protection, also known as Azure ATP) is a cloud-based security solution that leverages your on-premises Active Directory signals to identify, detect, and investigate advanced threats, compromised identities, and malicious insider actions directed at your organization.
Defender for Identity enables SecOps analysts and security professionals struggling to detect advanced attacks in hybrid environments to:
- Monitor users, entity behavior, and activities with learning-based analytics
- Protect user identities and credentials stored in Active Directory
- Identify and investigate suspicious user activities and advanced attacks throughout the kill chain
- Provide clear incident information on a simple timeline for fast triage
Defender for Identity architecture:
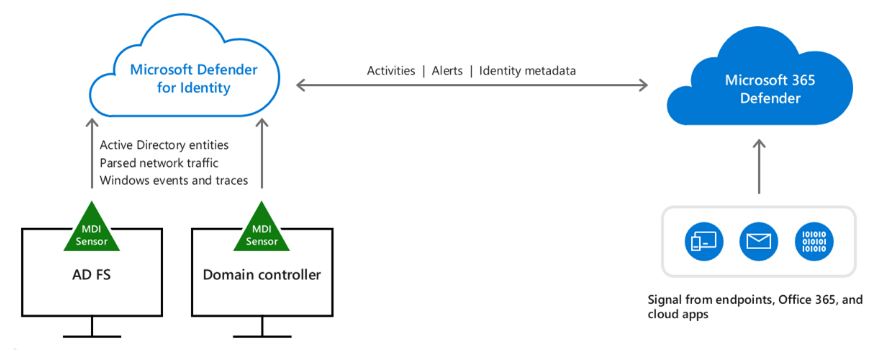
This section describes how the flow of Defender for Identity's network and event capturing works, and drills down to describe the functionality of the main components: the Defender for Identity portal, Defender for Identity sensor, and Defender for Identity cloud service.
Installed directly on your domain controller or AD FS servers, the Defender for Identity sensor accesses the event logs it requires directly from the servers. After the logs and network traffic are parsed by the sensor, Defender for Identity sends only the parsed information to the Defender for Identity cloud service (only a percentage of the logs are sent).
Defender for Identity Components
Defender for Identity consists of the following components:
2.1 Microsoft 365 Defender portal
The Microsoft 365 Defender portal creates your Defender for Identity instance, displays the data received from Defender for Identity sensors, and enables you to monitor, manage, and investigate threats in your network environment.
2.2 Defender for Identity sensor
Defender for Identity sensors can be directly installed on the following servers:
Domain controllers: The sensor directly monitors domain controller traffic, without the need for a dedicated server, or configuration of port mirroring.AD FS: The sensor directly monitors network traffic and authentication events.
2.3 Defender for Identity cloud service
Defender for Identity cloud service runs on Azure infrastructure and is currently deployed in the US, Europe, Australia East, and Asia. Defender for Identity cloud service is connected to Microsoft's intelligent security graph.
2. Alerts
Microsoft Documentation:https://docs.microsoft.com/en-us/defender-for-identity/suspicious-activity-guide?tabs=external
Lab setup
The first tutorial in this four part series walks you through creating a lab for testing Defender for Identity's discrete detections. The tutorial includes information about machines, users, and tools that are needed to set up the lab and complete its playbooks. The instructions assume you're comfortable setting up a domain controller and workstations for lab use along with other administrative tasks. The closer your lab is to the suggested lab setup, the easier it will be to follow Defender for Identity testing procedures. When your lab setup is complete, use the Defender for Identity Security Alert playbooks for testing.
Setup an ATP security alert lab
Reconnaissance playbook
The second tutorial in this four part series is a reconnaissance playbook. Reconnaissance activities allow attackers to gain a thorough understanding and complete mapping of your environment for later use. The playbook shows some of Defender for Identity's capabilities in identifying and detecting suspicious activities from potential attacks using examples from common, publicly available hacking and attack tools.
Lateral movement playbook
The lateral movement playbook is third in the four part tutorial series. Lateral movements are made by an attacker attempting to gain domain dominance. As you run this playbook, you'll see lateral movement path threat detections and security alerts services of Defender for Identity from the simulated lateral movements you make in your lab.
Domain dominance playbook
The last tutorial in the four part series is the domain dominance playbook. During the domain dominance phase, an attacker has already gained legitimate credentials to access your domain controller and attempts to achieve persistent domain dominance. You'll simulate some common domain dominance methods to see the domain dominance focused threat detection and security alert services of Defender for Identity.
3. Azure Sentinel Integration Connector
Microsoft Defender for Identity alerts are connected through the Microsoft 365 Defender connector and automatically grouped into incidents. Incidents can be seen in the incidents queue.
Query to see Microsoft Defender for Identity alerts
SecurityAlert | where ProductName == "Azure Advanced Threat Protection" | summarize arg_max(TimeGenerated, *) by SystemAlertId
SecurityAlert | where TimeGenerated > ago (365d)| where ProductName == "Azure Advanced Threat Protection"